“You can even completely hide your private folders from virtually all applications, and such folders would remain invisible until you enter a valid password.”
Is this really true?? No, not at all. Let’s see how. Actually, my friend used one of these softwares and challenged me if I can expose his data without the password used to lock the data. So, I decided to give it a try.
I first downloaded and installed a trial copy of Folder Guard software on my computer. Then I created a folder named “mysecretfiles” inside directory “test” on G: drive. Then, I opened Folder Guard, created a login password and locked this folder. The configuration setting I used for this folder was Access = “No Access” and Visibility = “Hidden”. You should see a similar screenshot after you lock a folder.
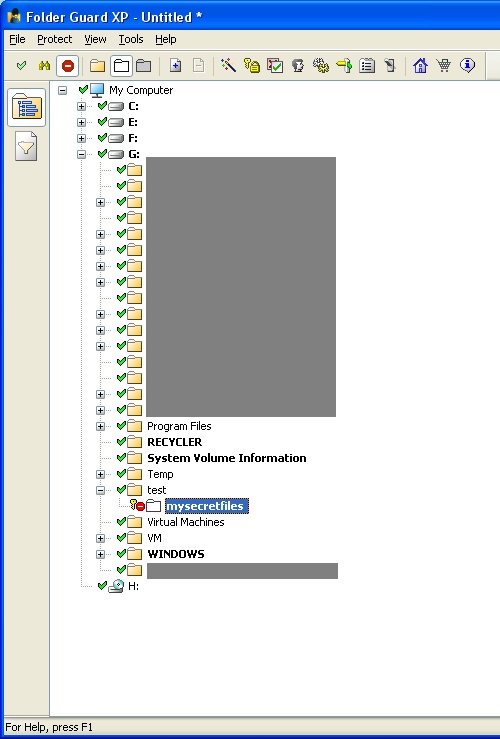
I closed Folder Guard and clicked on “Yes” in the “Start Protecting the System” dialog box. This caused Folder Guard to enable protection on my folder. As a result, I didn’t see my locked folder in Windows Explorer.

I tried to understand how these softwares work. Almost all of them placed hooks into the windows device drivers and block access calls to locked files and folders. This model is flawed because an attacker can use the back channel, often referred to as Direct Disk Access Mode.
So, I decided to fire my favorite Disk Editor WinHex and I could easily see and browse my locked folder with ease. I could look inside my locked file “mysensitivedata.txt” and check its contents with my username, password and SSN :). The other best part of this disk editor is that I don’t need to install it, I could just easily run it from a USB pen stick.

So, the best protection to protect your data is still to use industry standard encryption with algorithms such as AES, 3DES, etc. Even if the data falls in wrong hands, the confidentiality of the data won’t be compromised. Use softwares like TrueCrypt to protect your sensitive data.
]]>A web page is composed of three major content types, namely HTML content, Javascript Code and CSS styling code. I felt the need of a tool that could beautify or format the entire web page source code. I use Burp Suite, my favorite web proxy tool. However, it does not have source code formatting feature, it just colors the web page by choosing different colors for html tag names, html attribute values, javascript, css, etc.
I looked on the internet for free alternatives, but I could not find free tools that could format the entire web page. Most of them could only format either one of HTML or Javascript or CSS. So, I decided to write a perl script myself. I used the libraries HTML::Tidy by Dave Raggett and Javascript::Beautifier by Einars Lielmanis. And I have written my own CSS formatting code.
Example of HTML Formatting
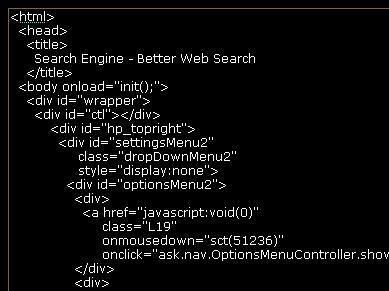
Example of CSS Formatting
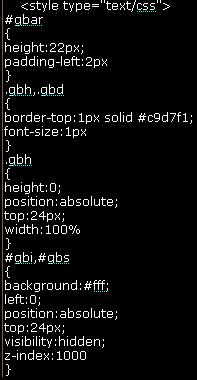
Example of Javascript Formatting
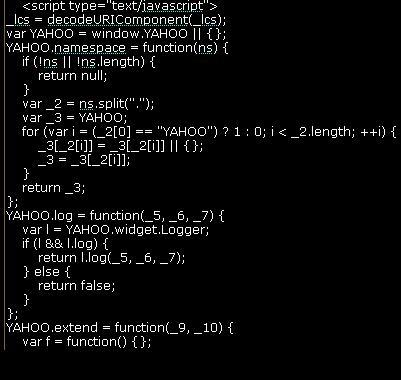
In addition, I have done one more improvement by formatting the javascript code in html event handlers. I picked the comprehensive event handlers list from XSS Attacks Book by RSnake, Jeremiah, Pdp, Anton Rager and Seth Fogie. Another excellent book to have on your shelf.
Example of Event Handler Code Formatting (see the onload and onclick event handlers)
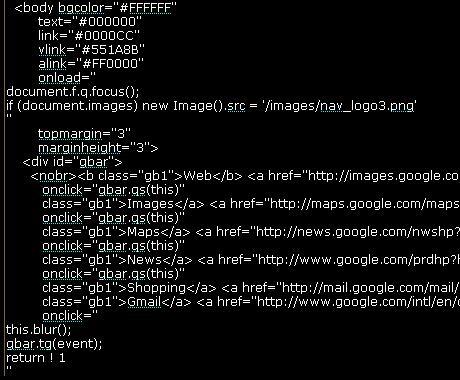
And finally the …
Inferno’s All-In-One HTML + Javascript + CSS Formatter
Paste your Source Code below
I would advise trying any of the search engines’ source code like google, yahoo, etc. Their code is highly compressed. If you have any problem using the text box above, try using this Link.
Plans for future additions include
* Add custom event handlers and variables (e.g. expr variable in Samy Worm Code)
* Javascript Deobfuscation
* More configuration Options
* Burp Proxy Plugin
Please provide your valuable suggestions to improve this tool. This tool is completely free for your use.
]]>In Billy’s Blog, two solutions have been discussed :-
Solution 1. Update to the latest version of JRE. This will protect you. However, if I am a web application writer, I cannot ensure that my customers will be protected. The reason is I cannot control the JRE version that my customers will be running on their client machines. The JRE updates don’t work like Windows Updates. So their obsolete JRE environments will not get automatically updated, which leaves them vulnerable to cross-domain exploits. So, Billy discusses another solution for the application writer.
Solution 2. Serve user controlled files from a “throw away” domain. However, having a separate domain might not be feasible at all times, for reasons such as cost, management issues, etc.
My Solution. This made me think of some solution that could help an application developer to filter malicious jar content on the server side. If the application is able to restrict the upload of malicious files, it solves the problem on the server side without worrying about which version of JRE the client is running. I found the api JarFile in Java library java.util.jar to be extremely useful. It takes as input a file parameter, and returns a JarFile object if the input file has jar content. Otherwise, it raises a java.util.zip.ZipException exception.
I have constructed Proof of Concept code that tests a input file for malicious jar content.
DetectGIFAR.java, DetectGIFAR.class, titanic.gif, evil.gif
Below is sample output
And if you are new to the GIFAR exploit, below is example html applet code that loads a malicious gif hosted on my domain. You need to have the vulnerable JRE 1.6 update 10 or lower to see this applet running. You can play with this applet by typing anywhere inside it :).
Let me know your thoughts and opinions on this server side fix. I am always open for discussions.
]]>I am “Inferno” from California, United States. I have just started my blog this week. It will be all about my research and knowledge in the application security area, especially concentrating on web application security.
I am deeply inspired by works of Security Researchers - Robert “RSnake” Hansen and Jeremiah Grossman, and follow their blogs closely, just like most people in the web app security space :).
My Email Address is Inferno {at} SecureThoughts.com
]]>