Well it is hard to believe, but the new version of Apple’s browser “Safari 4” still continues to be vulnerable to URL obfuscation techniques. All other browser vendors, whether it is Internet Explorer, Firefox, Opera or Chrome, have fixed this issue long time ago. However, everyone had fixed this issue using completely different solutions, which brings up the question that shouldn’t they follow a common standard ??
For those of you who don’t know what URL obfuscation is, it is an age old technique that phishers used to spoof legitimate websites like popular banks, etc. The phisher will send spam emails claiming to come from your bank and if you fall for the spoof, you might end up giving up your credentials. Among the popular techniques, this one I feel is the most important one as it tries to exploit link embedded authentication which is done using a url format http://username:[email protected]. An attacker can use overly long urls to completely hide the suspicious part in your address bar which is “@evilwebsite.com” or something like “@evilwebsiteip (xx.xx.xx.xx)” with different number encoding methods.
For my testing, I did the following: {Note: IP changed from last post, images have old IP}
1. I pasted this url in the browser’s address bar
2. I hovered on this hyperlink and noticed my STATUS BAR [Window Width should be <=1024]
Here are the results:
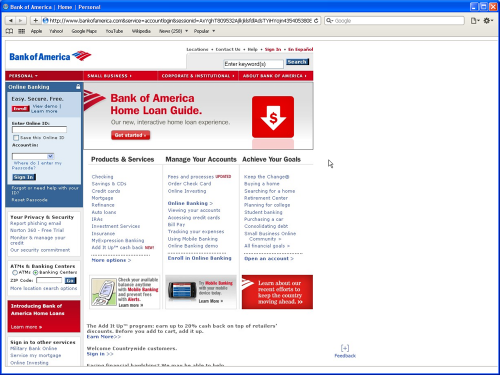
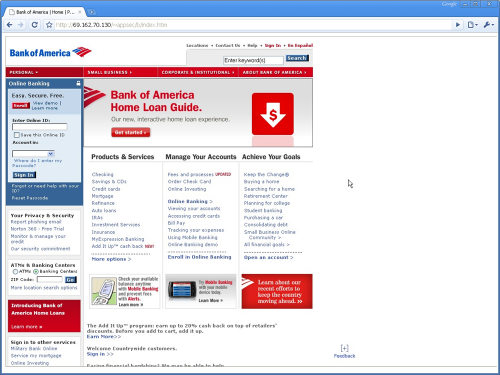
Safari 4.0 (530.17): Safari is vulnerable to this exploit. It does not take any steps to mitigate this problem. In the address bar, the overly long url continues to show as it is after the webpage is opened and hence a normal user is very likely to fall a prey to this phishing attack (see the image below). Also, status bar is disabled by default. Since most users don’t change the default settings, user is again more likely to fall prey when they click a hyperlink somewhere on the web. If you explicitly enabled the status bar, then you might identify the evil site. The reason being that Safari does a truncation on the long url by putting “..” in the middle, so you will see the suspicious part at the end.
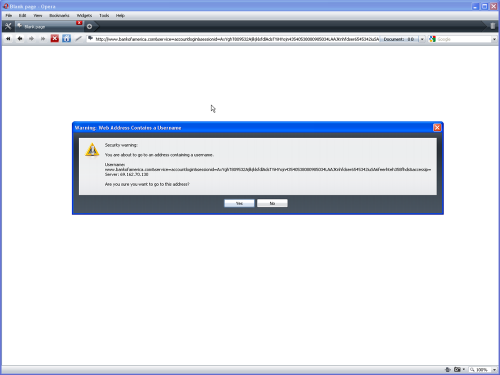
Opera 9.64: Opera has some mitigation strategies to protect against this exploit. It will raise a popup alerting the user that a username is entered as part of url. The username in error message can be a little confusing to the user and ideally it should instead put the name/ip of the evil site which is a better indicator (one that Firefox uses). Another sad part is “YES” button is the default option. So if a user does not understand the message or accidently presses “ENTER” (which most people do when they see popups), they might become a victim to this phishing attack. Regarding the status bar part, when you hover over a overly long hyperlink, Opera truncates it at the end (which is bad) so you won’t see the evil site information at the end of URL.
Chrome 2.0.172.31: The obfuscated URL works in Google Chrome, however Google has taken important mitigation steps to prevent phishing altogether. The first thing they do not display the “username:password@” portion of the URL when you hover over a link. The second thing they do is they strip out the “username:password@” portion of the URL when visiting that URL, so a user clearly sees the evil site name or ip. This definitely makes the user suspicious and hence won’t fall for the exploit. The last thing they do is they convert decimal addresses to dotted quad notation.
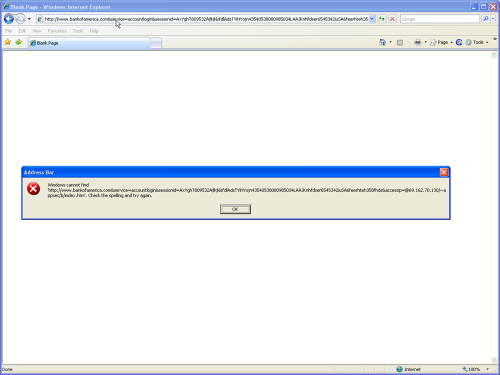
Internet Explorer 7.0.5730.13: Internet Explorer stopped supporting the link based authentication url format from IE7 onwards. Moreover, if you put these long urls in hyperlinks, they won’t work even if user clicks on them. So, YES, you are not vulnerable to this exploit in IE. However, I have a concern with the error message raised “Windows cannot find …” when a user tries to access such urls. I really feel that Microsoft should improve the content of this message, as otherwise, a normal user might think that IE is not able to open such urls and might try using other browsers like Safari, where they become a prey to his phishing attack.
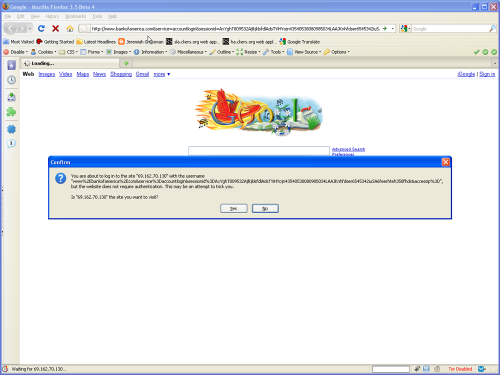
Firefox 3.5 Beta 4: Last, but not the least Firefox. I really like Firefox which intelligently decides the content of error messages. If your site does not support HTTP Basic Authentication, there cannot be any usecase of a user providing auth credentials. So, it raises an important message that you are being tricked. It also includes the evil site’s name or ip and confirms with you if you want to go there. Also, “NO” button is the default choice. There is almost 0% possibility of a person falling a prey to this phishing attack here. Regarding the status bar part, when you hover on a overly long hyperlink, Firefox truncates it at the end (just like Opera which is bad) so you won’t see the evil site information at the end of URL.
I feel that common mitigation techniques should be implemented uniformly in all browsers. If we combine the techniques used by Firefox and Chrome, we can get the best of both worlds which is to continue to support link based authentication and mitigating the security vulnerabilities arising from url obfuscation with overly long urls.
![[del.icio.us]](https://securethoughts.com/wp-content/plugins/bookmarkify/delicious.png)
![[Digg]](https://securethoughts.com/wp-content/plugins/bookmarkify/digg.png)
![[Facebook]](https://securethoughts.com/wp-content/plugins/bookmarkify/facebook.png)
![[Google]](https://securethoughts.com/wp-content/plugins/bookmarkify/google.png)
![[LinkedIn]](https://securethoughts.com/wp-content/plugins/bookmarkify/linkedin.png)
![[Reddit]](https://securethoughts.com/wp-content/plugins/bookmarkify/reddit.png)
![[StumbleUpon]](https://securethoughts.com/wp-content/plugins/bookmarkify/stumbleupon.png)
![[Technorati]](https://securethoughts.com/wp-content/plugins/bookmarkify/technorati.png)
![[Twitter]](https://securethoughts.com/wp-content/plugins/bookmarkify/twitter.png)
![[Yahoo!]](https://securethoughts.com/wp-content/plugins/bookmarkify/yahoo.png)