=============================================
| SECURETHOUGHTS.COM ADVISORY |
| - CVE-ID | : CVE-2009-3931 (Chrome) |
| - Release Date | : November 05, 2009 |
| - CVSS Severity | : 9.3 (High) |
| - Discovered by | : Inferno |
=============================================
I. TITLE
————————-
Using Blended Browser Threats involving Chrome to steal files on your computer
II. VULNERABLE
————————-
Chrome all versions < 3.0.195.32
Tests performed on v3.0.195.25
III. BACKGROUND
-------------------------
Google Chrome is a web browser released by Google which uses the WebKit layout engine and application framework. It is one of the four most popular browsers in the market today. Google released the entire source code of Chrome, including its bespoke V8 JavaScript engine as an open source project entitled Chromium, in 2008. Google Chrome is best known for its fast speed, simplicity and reliability.
IV. DESCRIPTION
-------------------------
Google Chrome has an inbuilt file downloader[1], just like every other browser. However, the behavior of this function is different from other browsers and provides users much more usability and convenience. Chrome automatically downloads a file from any site that is passed using the Content-Disposition header value “attachment” (on the contrary, all other browsers show a save as dialog). There are some mitigations done by Chrome to protect users from auto downloading malware by raising an alert on executable extensions such as .exe, .htm, .jar, etc.
The vulnerability arises from the fact that there are other extensions such as .svg, .mht, .mhtml that don’t exist in the Chrome’s malicious extension blacklist and hence the user never gets a warning message before they are auto downloaded to his or her computer. If these downloaded files are clicked from the Chrome’s download bar or Windows Explorer (which the user is highely likely to click considering his or her trust in Chrome that it warns for malicious extensions), they will automatically get opened in other browsers and can be used to steal any file on the user’s computer.
The reason for the name “Blended Browser Threats” is because here, Google Chrome is used as a vehicle for attack, whereas the real vulnerability executes inside other browsers such as IE6, Safari on your computer. The vulnerability is not directly exploitable in IE6, Safari since an evil site cannot automatically download content on your computer without your permission. Another important point to note here is you might not be using the browsers IE6, Safari and instead using Chrome. But clicking a particular file on Chrome’s download bar can make it automatically open in IE6, Safari. See the proof of concept examples below.
V. PROOF OF CONCEPT
————————-
1. The MHT, MHTML (MIME HTML) file format is used by Internet Explorer to embed all external resources, usually images, in a single document. Basically, whenever you click “Save As” on a web page, this is the default format used to save it. So, MHT, MHTML files gets automatically opened in IE when clicked. The exploit I want to discuss is interesting in the context of IE6 (estimated to be installed on roughly 25% of the computers). For other newer versions like IE7, IE8, the user is explicitly prompted about the danger of executing javascript and hence much harder to exploit.
An evil site opened inside Chrome can automatically download a MHT/MHTML file to your computer. If the user clicks on this downloaded file from the Chrome’s download bar or opens this file through Windows Explorer, it gets automatically opened in IE6. The malicious script executes and can be used to send any of your local files to a remote evil destination. Ex: Click on this link-
http://securethoughts.com/security/chromelocalfilexss/chromedownload.php?fname=WATCHMENAKED.mhtml
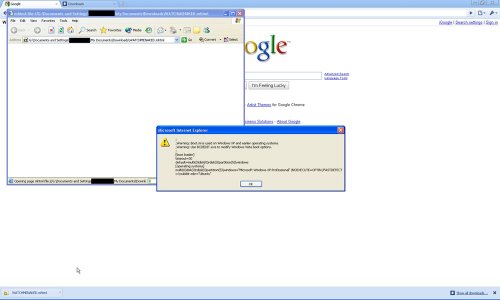
2. The SVG(Scalable Vector Graphics) file is a registered extension in some Safari versions and hence a SVG file gets automatically opened in Safari. If you ever had an older version of Safari on your computer, this extension will be most probably there in your registry. Hence, it does not matter what your current version of Safari is (and you may very well be using the latest version of Safari). So the exploit works like this:
An evil site opened inside Chrome can automatically download a SVG file to your computer. If the user clicks on this downloaded file from the Chrome’s download bar or opens this file through Windows Explorer, it gets automatically opened in Safari. The malicious script executes and can be used to send any of your local files to a remote evil destination. Ex: Click on this link-
http://securethoughts.com/security/chromelocalfilexss/chromedownload.php?fname=WATCHMENAKED.svg
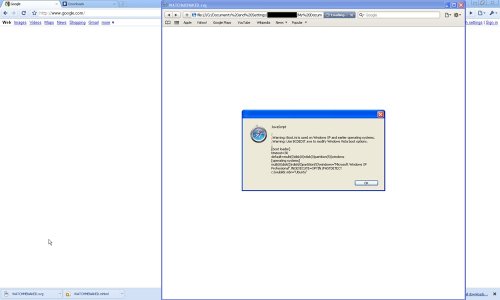
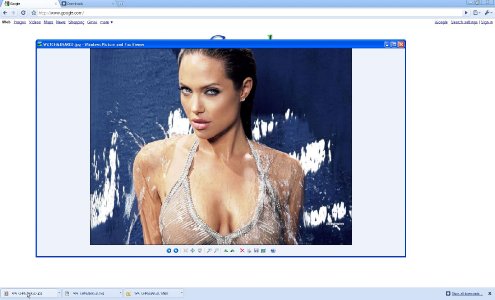
3. An evil site opened inside Chrome can automatically download inappropriate content such as a por_ographic image to your computer. Ex: Click on this link-
http://securethoughts.com/security/chromelocalfilexss/chromedownload.php?fname=WATCHMENAKED.jpg
VI. FIX DESCRIPTION
————————-
Google Chrome Team fixed this vulnerability by appending these dangerous extensions such as .mht, .mhtml, .svg, etc to already existing extension blacklist.
Check out the fixes done in Chromium Source Code here [2,3].
Chrome Team is also actively looking how to improve this mechanism in the long run, but because of the need to maintain compatibility with certain existing uses, this needs to be done carefully.
VII. SOLUTION
————————-
Chrome: Upgrade to latest version of Google Chrome (v3.0.195.32 or higher). If you remain connected to the internet, this should be automatic.
The more secure solution is to configure your browser to prompt you explicitly before downloading any file type. This can be done by going to Chrome Configuration Options -> Under the Hood -> Check the ‘Ask where to save each file before downloading‘ flag.
VIII. References
————————-
1. Downloads: Downloading a file – Google Chrome Help
http://www.google.com/support/chrome/bin/answer.py?hl=en&answer=95759
2. Google Chrome Code Fix 1
http://codereview.chromium.org/243115
3. Google Chrome Code Fix 2
http://codereview.chromium.org/261022
4. Interesting Reads – thanks to Michal.
(a) Security in Depth: Local Web Pages – Adam Barth
http://blog.chromium.org/2008/12/security-in-depth-local-web-pages.html
(b) Same-Origin Policy:Browser Security Handbook – Michal Zalewski
http://code.google.com/p/browsersec/wiki/Part2#Same-origin_policy
IX. CREDITS
————————-
This vulnerability is discovered by
Inferno (inferno {at} securethoughts {dot} com)
X. DISCLOSURE TIMELINE
————————-
Oct 5, 2009 12:14 AM: Vulnerability reported to Google Security Team.
Oct 6, 2009 11:19 AM: Automated Response from Google Security Team.
Oct 6, 2009 01:46 PM: First Status update provided by Michal Zalewski. Vulnerability confirmed.
Oct 6, 2009 11:33 PM: Second Status update provided by Michal Zalewski. Code Fix 1 checked in by Adam Barth.
Oct 8, 2009 12:30 AM: Code Fix 2 checked in by Adam Barth.
Nov 5, 2009 01:18 PM: Chrome v3.0.195.32 Released containing the Security Patch.
I would like to thank Michal Zalewski and Adam Barth from Google for their prompt responses and getting the patch ready in a timely manner. It was a pleasure working with them. I am grateful to Google for providing credit for my research by listing me on their “We Thank You” Page.
![[del.icio.us]](https://securethoughts.com/wp-content/plugins/bookmarkify/delicious.png)
![[Digg]](https://securethoughts.com/wp-content/plugins/bookmarkify/digg.png)
![[Facebook]](https://securethoughts.com/wp-content/plugins/bookmarkify/facebook.png)
![[Google]](https://securethoughts.com/wp-content/plugins/bookmarkify/google.png)
![[LinkedIn]](https://securethoughts.com/wp-content/plugins/bookmarkify/linkedin.png)
![[Reddit]](https://securethoughts.com/wp-content/plugins/bookmarkify/reddit.png)
![[StumbleUpon]](https://securethoughts.com/wp-content/plugins/bookmarkify/stumbleupon.png)
![[Technorati]](https://securethoughts.com/wp-content/plugins/bookmarkify/technorati.png)
![[Twitter]](https://securethoughts.com/wp-content/plugins/bookmarkify/twitter.png)
![[Yahoo!]](https://securethoughts.com/wp-content/plugins/bookmarkify/yahoo.png)